100% Pass IT Exam By Training Lead2pass New VCE And PDF Dumps
100% Pass Lead2pass Practice Test Free Version
[April 2018] Lead2pass CompTIA CS0-001 VCE And PDF Instant Download 85q
Lead2pass New Updated CS0-001 Braindump Free Get:
https://www.lead2pass.com/cs0-001.html
QUESTION 21
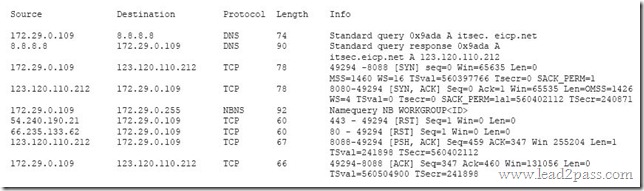
Review the following results:
Which of the following has occurred?
A. This is normal network traffic.
B. 123.120.110.212 is infected with a Trojan.
C. 172.29.0.109 is infected with a worm.
D. 172.29.0.109 is infected with a Trojan.
Answer: A
QUESTION 22
A security analyst is creating baseline system images to remediate vulnerabilities found in different operating systems. Each image needs to be scanned before it is deployed.
The security analyst must ensure the configurations match industry standard benchmarks and the process can be repeated frequently.
Which of the following vulnerability options would BEST create the process requirements?
A. Utilizing an operating system SCAP plugin
B. Utilizing an authorized credential scan
C. Utilizing a non-credential scan
D. Utilizing a known malware plugin
Answer: A
QUESTION 23
A network technician is concerned that an attacker is attempting to penetrate the network, and wants to set a rule on the firewall to prevent the attacker from learning which IP addresses are valid on the network. Which of the following protocols needs to be denied?
A. TCP
B. SMTP
C. ICMP
D. ARP
Answer: C
QUESTION 24
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port.
Which of the following should the analyst use?
A. Wireshark
B. Qualys
C. netstat
D. nmap
E. ping
Answer: C
QUESTION 25
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis.
The last completed scan of the network returned 5,682 possible vulnerabilities.
The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues.
Which of the following is the BEST way to proceed?
A. Attempt to identify all false positives and exceptions, and then resolve all remaining items.
B. Hold off on additional scanning until the current list of vulnerabilities have been resolved.
C. Place assets that handle PHI in a sandbox environment, and then resolve all vulnerabilities.
D. Reduce the scan to items identified as critical in the asset inventory, and resolve these issues first.
Answer: D
QUESTION 26
An administrator has been investigating the way in which an actor had been exfiltrating confidential data from a web server to a foreign host.
After a thorough forensic review, the administrator determined the server’s BIOS had been modified by rootkit installation.
After removing the rootkit and flashing the BIOS to a known good state, which of the following would BEST protect against future adversary access to the BIOS, in case another rootkit is installed?
A. Anti-malware application
B. Host-based IDS
C. TPM data sealing
D. File integrity monitoring
Answer: C
QUESTION 27
A security analyst is reviewing the following log after enabling key-based authentication.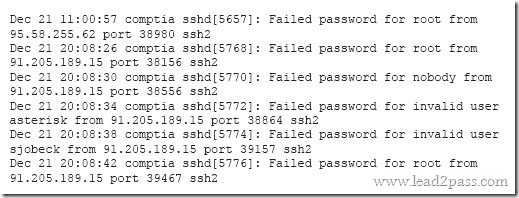
Given the above information, which of the following steps should be performed NEXT to secure the system?
A. Disable anonymous SSH logins.
B. Disable password authentication for SSH.
C. Disable SSHv1.
D. Disable remote root SSH logins.
Answer: B
QUESTION 28
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack.
Which of the following would be the BEST action for the cybersecurity analyst to perform?
A. Continue monitoring critical systems.
B. Shut down all server interfaces.
C. Inform management of the incident.
D. Inform users regarding the affected systems.
Answer: C
QUESTION 29
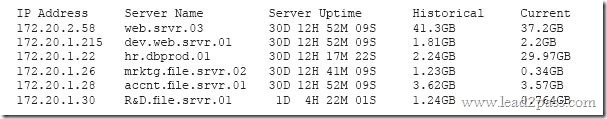
A security professional is analyzing the results of a network utilization report. The report includes the following information:
Which of the following servers needs further investigation?
A. hr.dbprod.01
B. R&D.file.srvr.01
C. mrktg.file.srvr.02
D. web.srvr.03
Answer: B
QUESTION 30
A cybersecurity analyst has several SIEM event logs to review for possible APT activity.
The analyst was given several items that include lists of indicators for both IP addresses and domains.
Which of the following actions is the BEST approach for the analyst to perform?
A. Use the IP addresses to search through the event logs.
B. Analyze the trends of the events while manually reviewing to see if any of the indicators match.
C. Create an advanced query that includes all of the indicators, and review any of the matches.
D. Scan for vulnerabilities with exploits known to have been used by an APT.
Answer: B
CS0-001 dumps full version (PDF&VCE): https://www.lead2pass.com/cs0-001.html
Large amount of free CS0-001 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDSG1XT3dzV0xVbDQ
admin April 16th, 2018
Posted In: CompTIA, CS0-001 Dumps, CS0-001 Exam Questions, CS0-001 New Questions, CS0-001 PDF, CS0-001 VCE
Tags: CS0-001 braindumps, CS0-001 exam dumps, CS0-001 exam question, CS0-001 pdf dumps, CS0-001 practice test, CS0-001 study guide, CS0-001 vce dumps, Lead2pass CS0-001